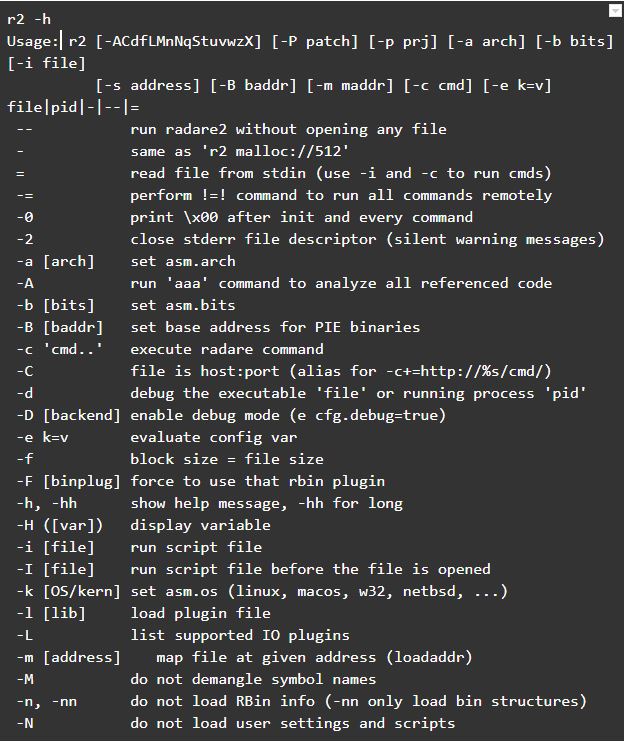
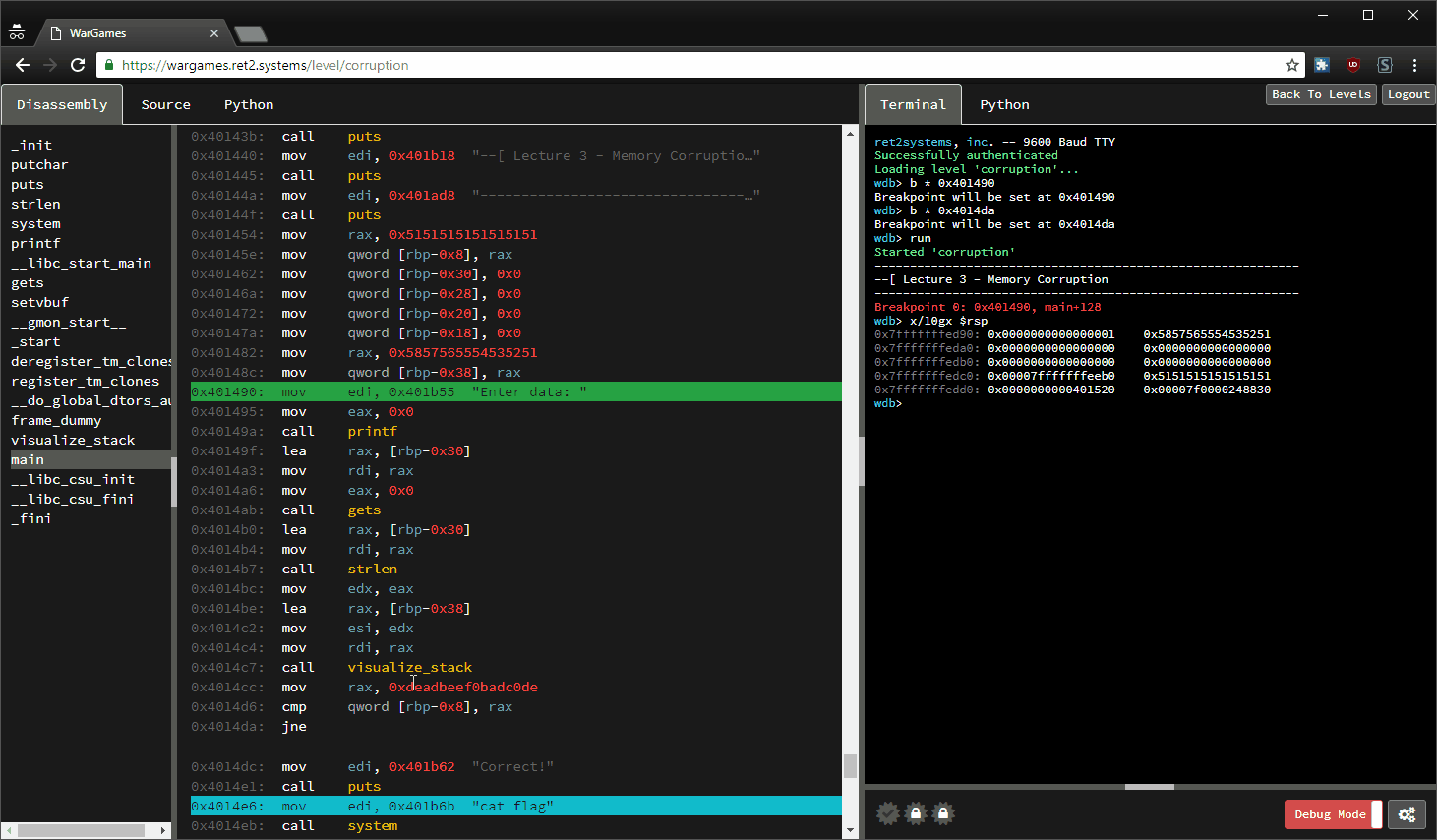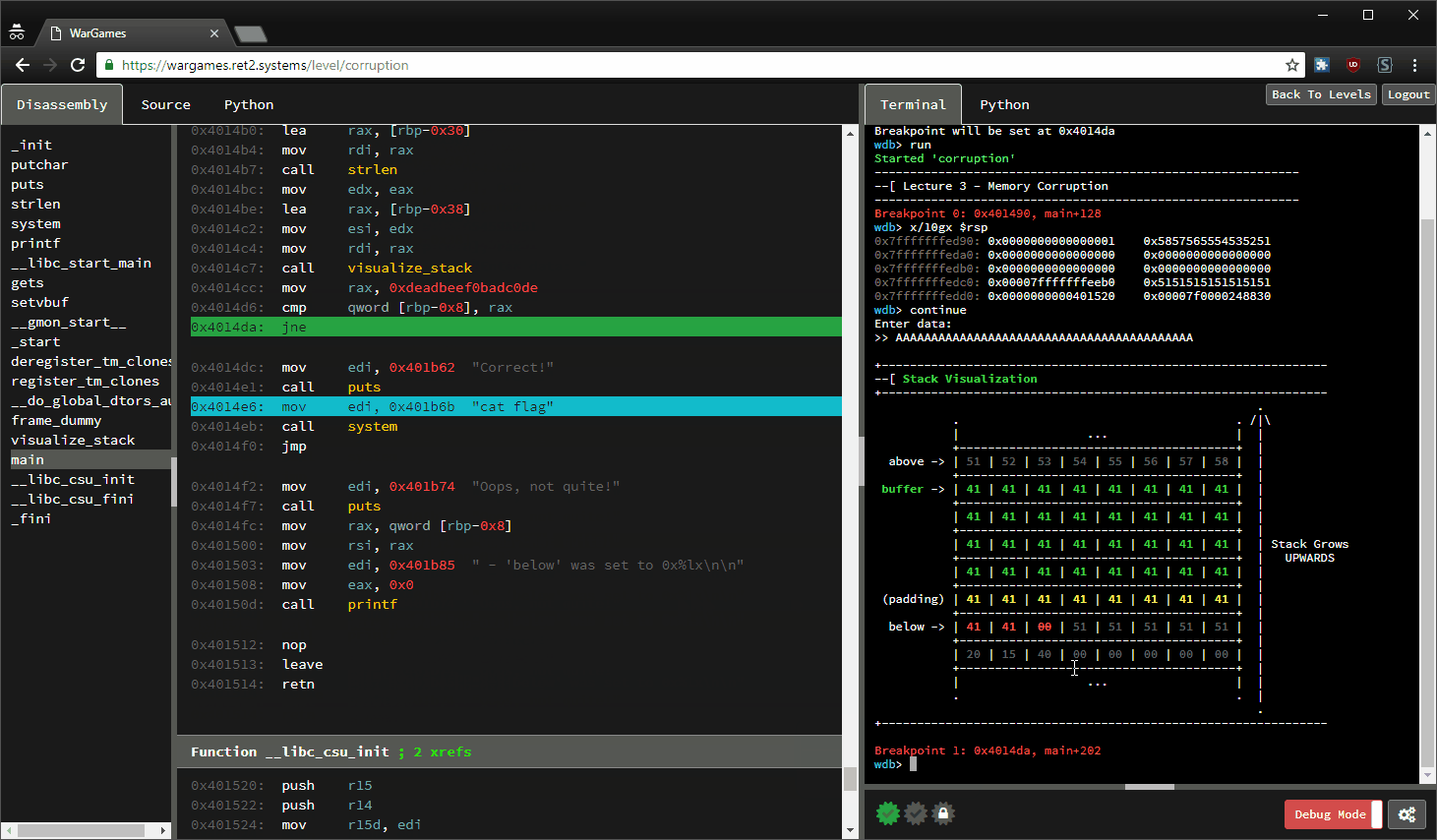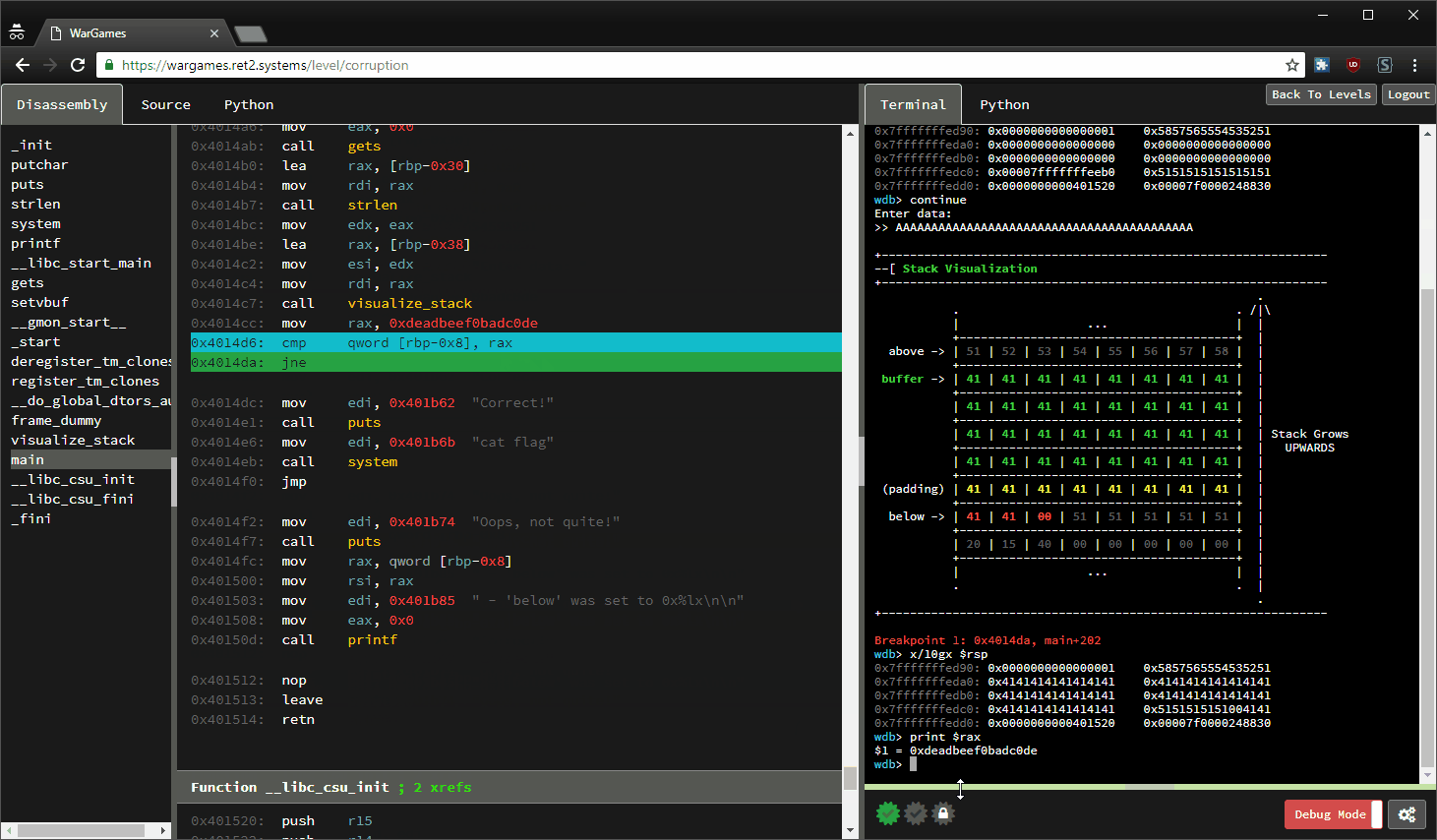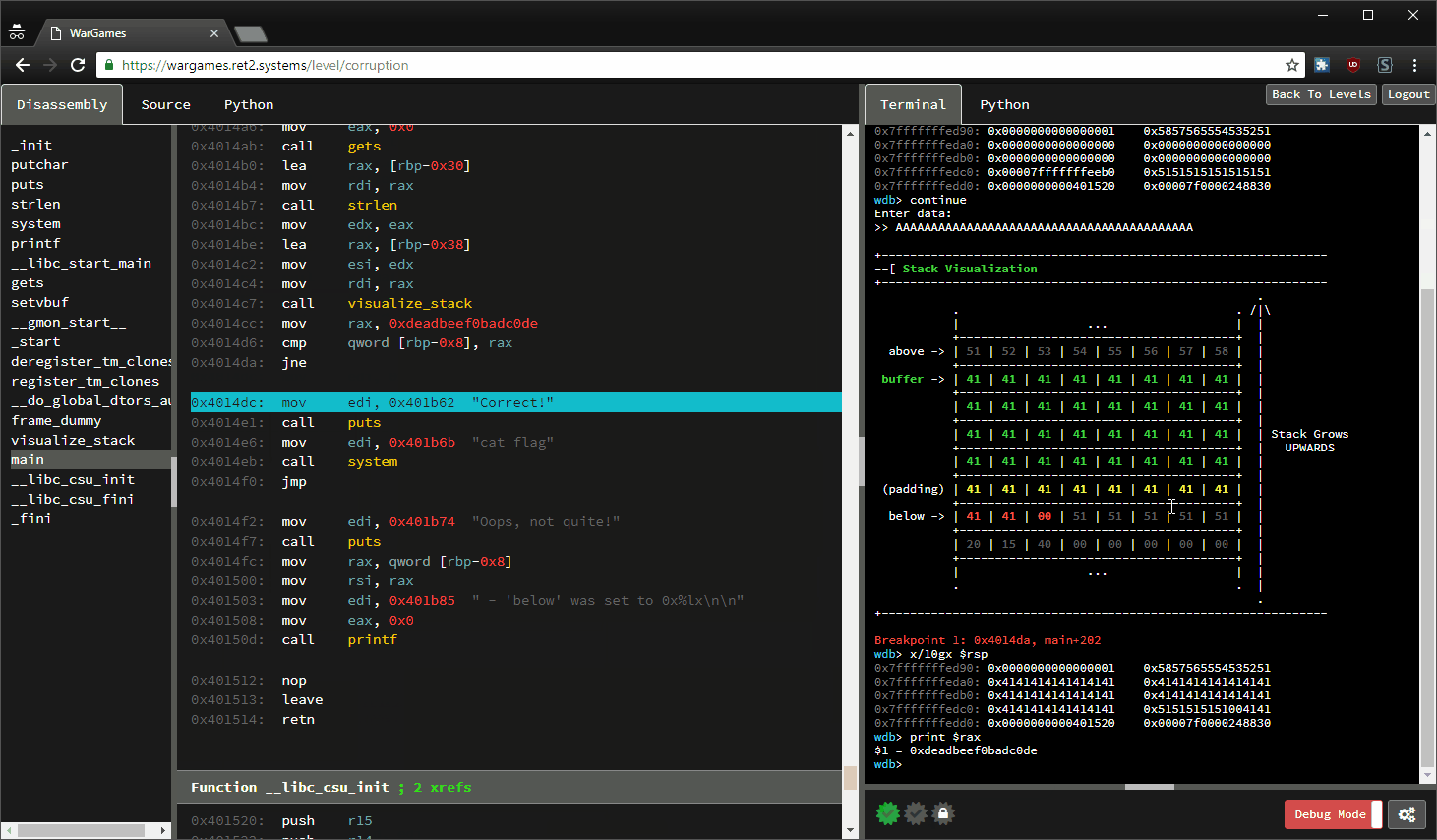
GitHub - crake7/Binary-Exploitation-Tools: Automation of buffer overflows corrupting the Saved Return Pointer.
Useless Crap? No, not nearly! Advance your binary exploitation skills by solving a sophisticated CTF challenge – HackMag

Amazon.fr - Practical Binary Analysis: Build Your Own Linux Tools for Binary Instrumentation, Analysis, and Disassembly - Andriesse, Dennis - Livres