Effective Security Monitoring Plan Cybersecurity Monitoring Implemented Ppt Example | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
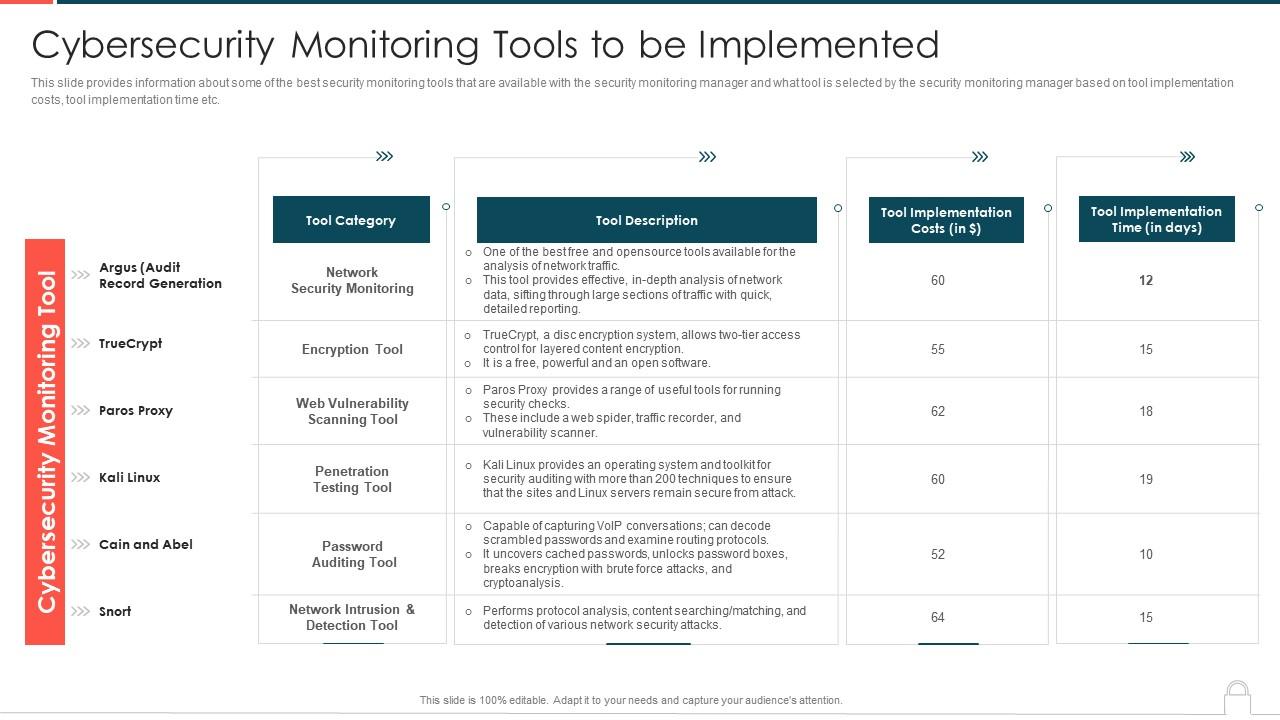
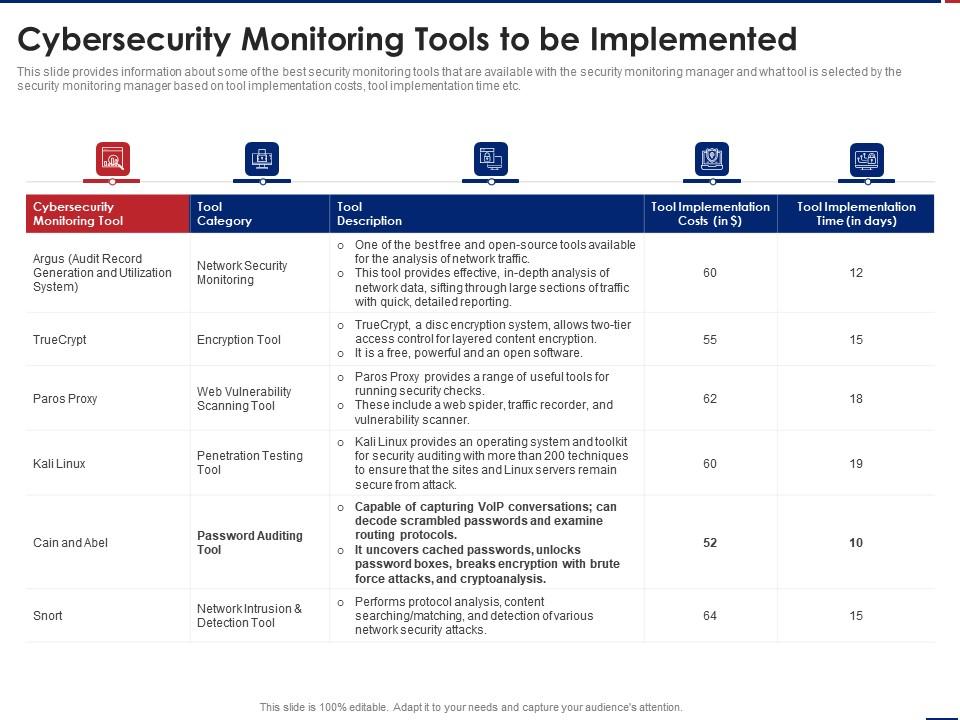
Ways To Set Up An Advanced Cybersecurity Monitoring Plan Cybersecurity Monitoring Tools To Be Implemented | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

NSA, CISA, and MS-ISAC Release Guidance for Securing Remote Monitoring and Management Software > National Security Agency/Central Security Service > Press Release View












![Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES] Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]](https://www.cimcor.com/hubfs/Cybersecurity%20Lifecycle.jpg)






![Top 20+ Cyber Security Tools for 2023 [Paid+Free] Top 20+ Cyber Security Tools for 2023 [Paid+Free]](https://intellipaat.com/blog/wp-content/uploads/2021/06/Top-20-Cyber-Security-Tools-Big.png)